Because you shouldn’t wait for a hacker to show you where your app is expose

If you’re running apps behind the Edgenexus Application Delivery Platform (Load-Balancer + WAF), you deserve a hacking playground. Enter the Damn Vulnerable Web Application (DVWA), a purposely vulnerable web application built for security pros, developers and dev-ops teams to flex their testing tools, harden configurations, and prove your posture is tighter than last year’s code-review.
DVWA is a PHP/MySQL web app designed to be… well… damn vulnerable. Its goal: give you a legal, realistic environment to test how real-world web vulnerabilities exploit systems, and in turn, how your protection stack responds.
Looxy.io is our recommended external testing tool. It can run a variety of Security (and other tests).
Best of all its free! looxy.io
The ALB-X has the ability to run containerised applications that can be join together directly or by using the load balancer proxy. This image has 1 already deployed Add-On but you can always go to Appstore the and deploy more.
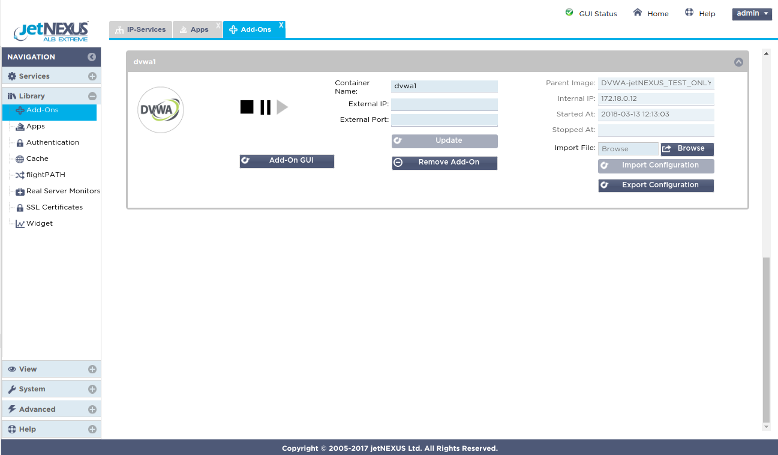
Virtual machines deployed in the Azure cloud make use of private internal IP addressing (NAT’ed IP’s) in the same way as would be deployed in a standard data centre environment.

Add-On applications deployed on the ALB-X communicate with ALB-X through an internal docker0 network interface. They are automatically allocated IP addresses from the internal docker0 pool.
A host name for each instance of Add-On application is configured through the ALB-X GUI prior to starting the application. The ALB-X is able to resolve the docker0 IP address for the application using this internal host name. Always use the host name when addressing the application containers – IP’s may change!
When you request a test drive a new instance of the DVWA test appliance is created in Azure.
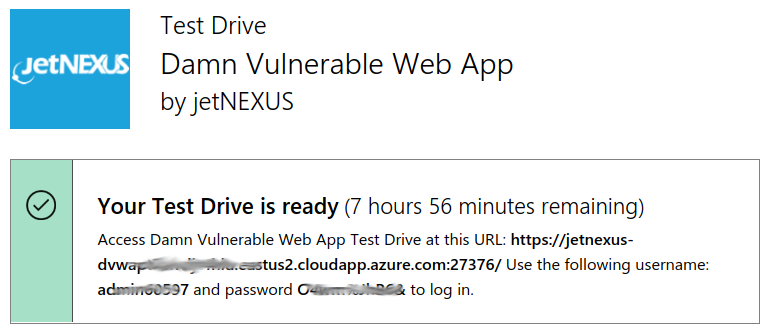
We recommend using the Chrome browser for this purpose. Access the Server
https://host name:27376
Click on Library in the left menu and select Add-Ons. Here you can see the DVWA Add-On that has been deployed on the ALB-X platform.
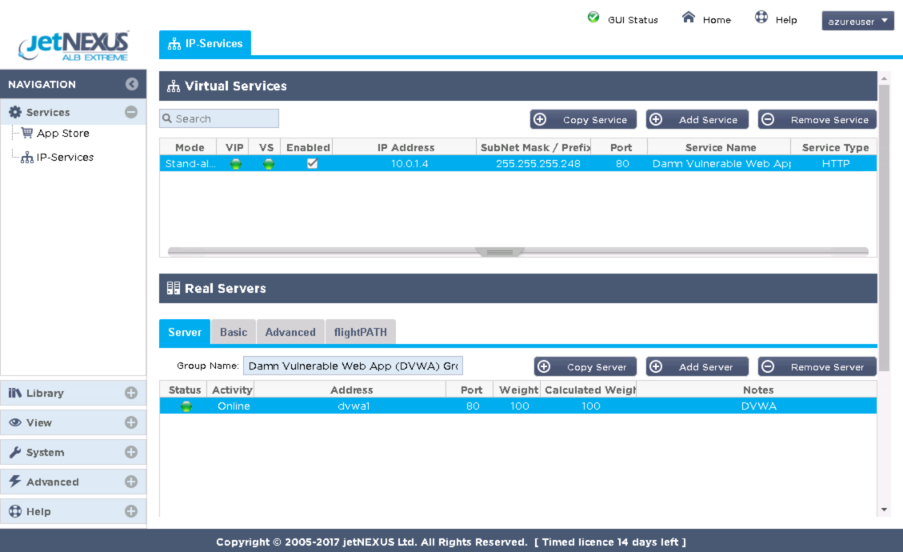
It has been configured with a container or host name dvwa1 and you can see the 172.x.x.x dynamic docker0 IP address that was allocated when the application was started.

As it is the DVWA functionality that you are interested in it would make sense now to take a look at the DVWA GUI. The DVWA as you can see from the IP services naming runs on port 80.
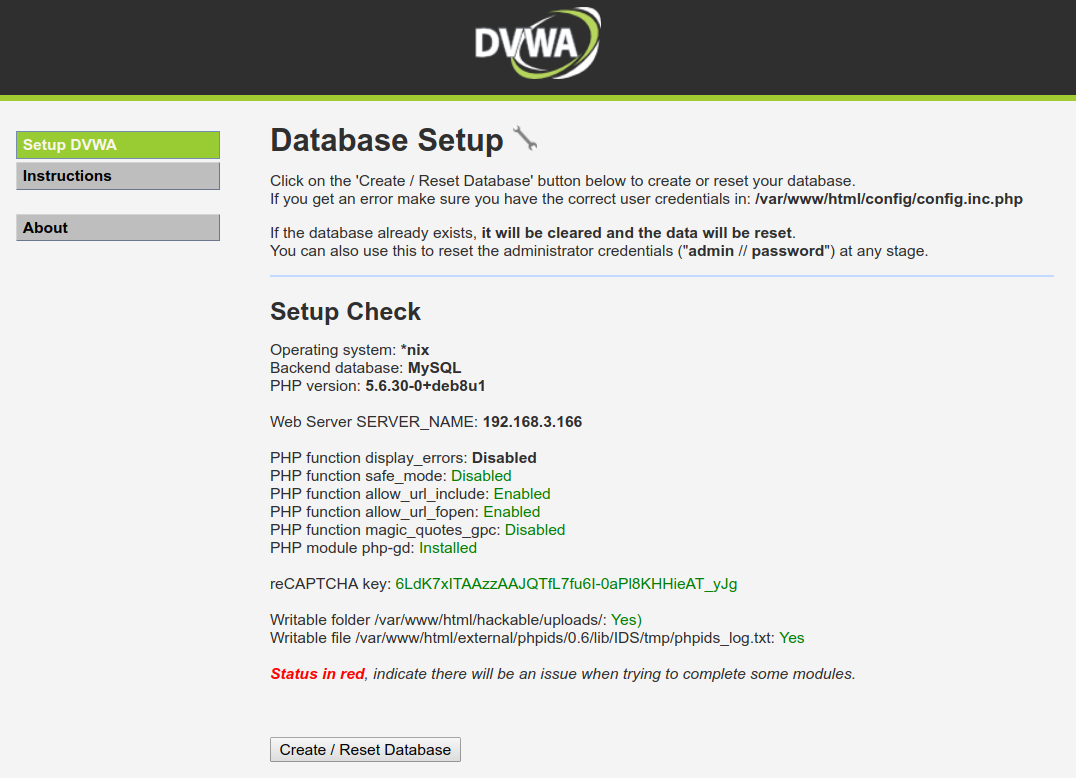
Click on Create / Reset Database
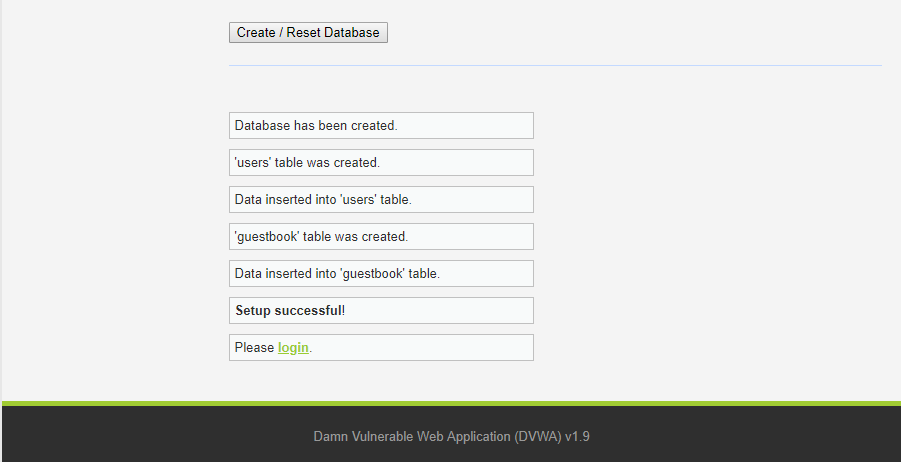

The default security level for DVWA is “Impossible” so it will not exhibit any vulnerabilities.
We will try exploiting one of the DVWA vulnerabilities. As we can see there is a page in DVWA where we can ping any IP address. Let’s check whether DVWA performs input parameters validation in “Low” security mode. Enter “127.0.0.1; cat /etc/passwd” in the IP address input field.
Voilà, we have successfully injected an arbitrary command and got a list of users registered in the operating system.
Damn Vulnerable Web App (DVWA)
A configurable Target web server that can be used to test your WAF and Attack tool
ZAP Web Application Attack Tool
Web Application Attack Tool is a vulnerability scanner based on OWASP ZAP
Hardware, software or even your own online image complete with a full test environment.
Just let us know what you need here